refer to: https://github.com/smartdec/smartcheck
https://www.getsecureworld.com/blog/top-10-solidity-smart-contract-audit-tools/
安装
npm install @smartdec/smartcheck -g
使用
进入到项目目录。
smartcheck -p .
例如,对这个sol, 就
contract EtherStore {
uint256 public withdrawalLimit = 1 ether;
mapping(address => uint256) public lastWithdrawTime;
mapping(address => uint256) public balances;
// 存款
function depositFunds() public payable {
balances[msg.sender] += msg.value;
}
// 提款
function withdrawFunds (uint256 _weiToWithdraw) public {
require(balances[msg.sender] >= _weiToWithdraw);
// limit the withdrawal
require(_weiToWithdraw <= withdrawalLimit);
// limit the time allowed to withdraw
require(now >= lastWithdrawTime[msg.sender] + 1 weeks);
require(msg.sender.call.value(_weiToWithdraw)()); // 这里应该使用transfer
balances[msg.sender] -= _weiToWithdraw; // 这一步有漏洞,上面一行使用了call
lastWithdrawTime[msg.sender] = now;
}
}
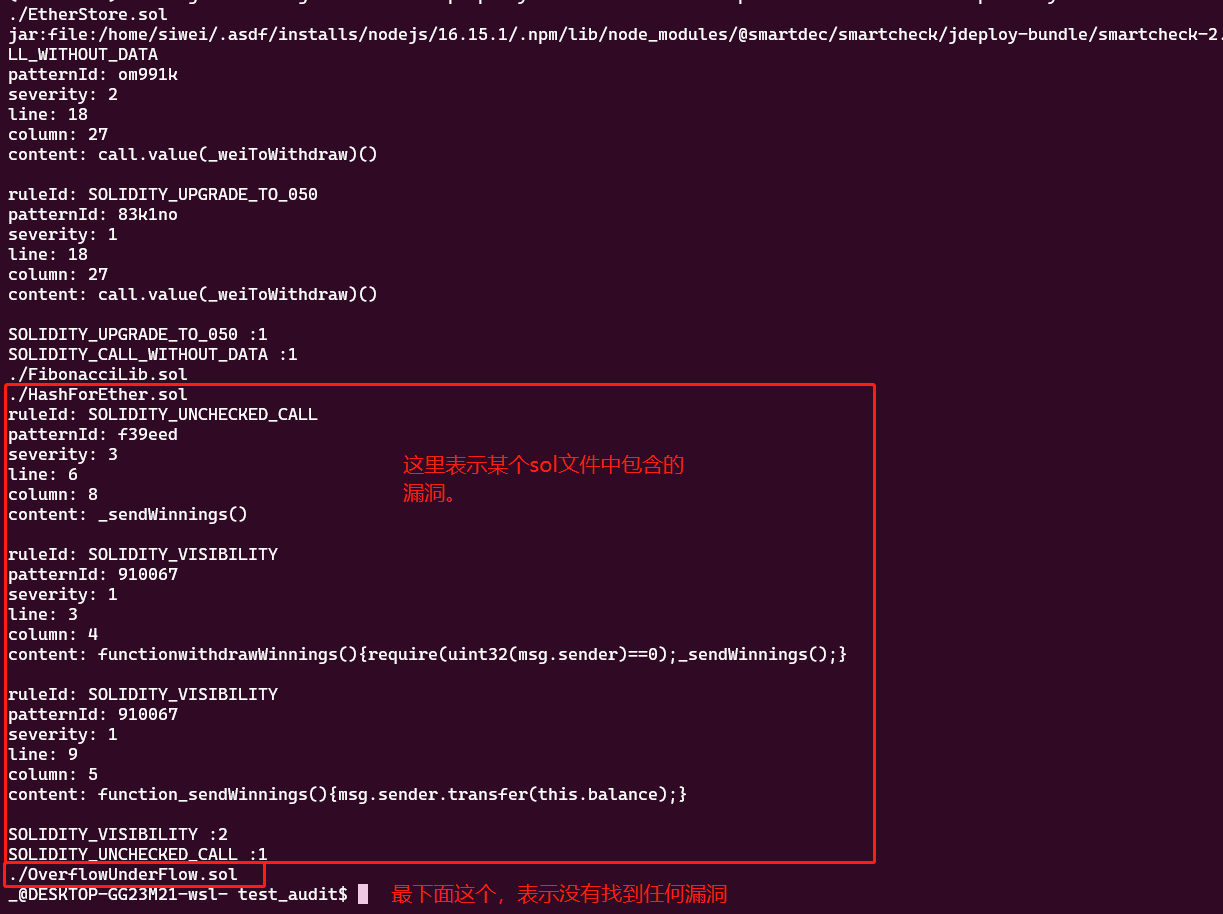
审查结果为:
Installing/Updating JRE in /home/siwei/.jdeploy... npm WARN deprecated har-validator@5.1.5: this library is no longer supported npm WARN deprecated uuid@3.4.0: Please upgrade to version 7 or higher. Older versions may use Math.random() in certain circumstances, which is known to be problematic. See https://v8.dev/blog/math-random for details. npm WARN deprecated request@2.88.2: request has been deprecated, see https://github.com/request/request/issues/3142 npm WARN deprecated node-jre@0.2.3: discontinued added 81 packages, and audited 82 packages in 23s 3 packages are looking for funding run `npm fund` for details 4 moderate severity vulnerabilities Some issues need review, and may require choosing a different dependency. Run `npm audit` for details. ./EtherStore.sol jar:file:/home/siwei/.asdf/installs/nodejs/16.15.1/.npm/lib/node_modules/@smartdec/smartcheck/jdeploy-bundle/smartcheck-2.0-jar-with-dependencies.jar!/solidity-rules.xmlruleId: SOLIDITY_CALL_WITHOUT_DATA patternId: om991k severity: 2 line: 18 column: 27 content: call.value(_weiToWithdraw)() ruleId: SOLIDITY_UPGRADE_TO_050 patternId: 83k1no severity: 1 line: 18 column: 27 content: call.value(_weiToWithdraw)() SOLIDITY_UPGRADE_TO_050 :1 SOLIDITY_CALL_WITHOUT_DATA :1
最关键的就是下面的2个。
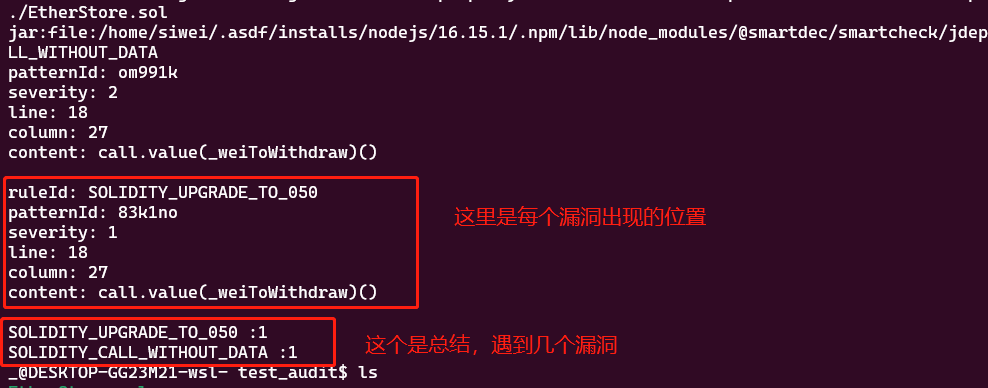
然后,我们查一下 这2个都是啥。
1. SOLIDITY_UPGRADE_TO_050 这个是可以被忽略的(ignore)
2. SOLIDITY_CALL_WITHOUT_DATA 这个是 re-entrancy (重入漏洞)
这个结果来自于这里:
https://github.com/smartbugs/smartbugs/wiki/Vulnerabilities-mapping